One late evening, we decided to take a look at Neckermann’s website, and we’ve discovered some critical vulnerabilites in the end. Sadly, Neckermann does not like to thank people reporting serious flaws.
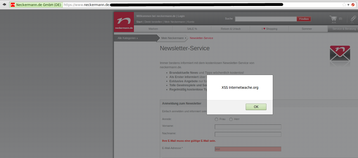
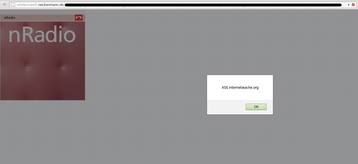
As always, we’ve discovered a cross site scripting issue. This time it was located in the “holidays”-area of the website, what could have turned a nice trip into a harmful phishing incident. It’s very common that search boxes are vulnerable to XSS attacks. Neckermann’s web developer did the same mistake and forget to sanitize the user’s input, which results in the XSS.
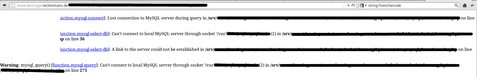
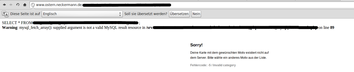
In the title we promised a critical vulnerablity.This does not mean that you should consider XSS as non-critical, but in our opinion SQL injection problems are far more critical than XSS flaws. The e-card system which allowed odinary users to sent easter greeting cards to their friends, was vulnerable to a SQL injection attack. An attacker could have abused this issue to read abitary data from the database. The german law forbids further testing, so that we can’t say which data may have been accessible by the attacker.
However, we contacted the vendor on 23th of June 2012. Even though we did not receive any response from the vendor, they’ve fixed the problems by deleting the whole content under the affected domains. Because of the fact, that we did not receive any response from Neckermann, we cannot say anything about the time frames.
The team of internetwache.org
Screenshots