During another testing session we decided to check out some banking websites. As a result we discovered some security shortcomings on their website.
Nowadays, nearly every major bank offers online banking, which allows their customers to the usual things like bank transfers and/or checking the account’s balance. Trojans and phishing pages are sometimes very interested in your credit card details and that’s why you need to be careful when doing online banking. You can find a lot of cheap credit card details in certain forums.
Correction: Sparkasse does not offer online banking services on the sparkasse.de domain. It’s only a content-platform. (Update: 27th of September, 2012)
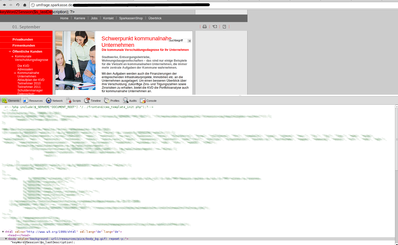
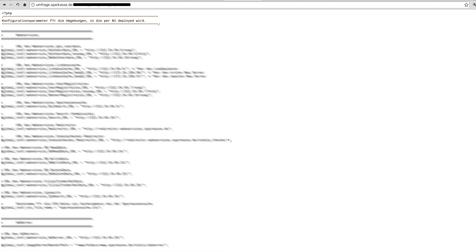
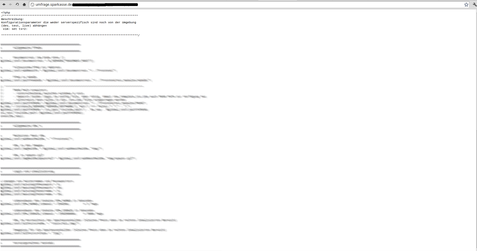
First of all, we’ve discovered some pages, which voluntarly disclosed their php source code. Even the configuration files with a “.php” ending have not been interpreted by the php engine. Regarding to the comments in the source code it’s last update was in 2009. We hope that this misconfiguration have not been present since then. Otherwise it would have been a nice starting point for crimial hackers.
Other debug/misconfiguration issue has been encountered under the “contentangebote” subdomain. A page printed all used variables containing sensitiv information in a manner that var_dump() does. Such error or debug information should be written into a logfile on a productive system and the visitor should see a user-friendly “an error has occured” page.
Last but not least there has been a path traversal-like bug on their main page. Unfortunatly, you could not include other files than the predefined template files, but you could brute-force the relative path up to the document root.
On 23th of September we contacted the Sparkasse via their Twitter customer help account. We sent them a PoC (proof-of-concept), which was stored in a password-protected txt file, because messages limited to 140 characters are surely to short for a complete security report. Sparkasse did a great and - especially fast - job fixing the issue located under the subdomain “umfrage”. The content was completly removed from the webserver. The other issues were fixed one day later.
The team of the Sparkasse thanked us for the advice and we were also happy, that the Sparkasse acted that quick.
The team of internetwache.org
Screenshots