A while ago we did some research about industrial control systems (ICS) and found a file named “photo.scr” on some of those. We want to share what we’ve learned about this file in this blogpost - in order to make sure that people find out how the malware works and how you can protect yourself from such a threat.
At the beginning we were not sure about the “photo.scr”. We discovered the file in all folders on some systems and there was also an autodownload starting when we tried to open a HTML-file (the help-file of an ICS-software). That was the point when we decided to take a deeper look at it. Not much time passed before we found out that the file belongs to a cryptomining-botnet which was also covered by some security companies in other publications.
We already decribed some results in a german article on the IT-news site golem.de: Kritische Infrastrukturen: Wenn die USV Kryptowährungen schürft
For the analysis we maily used the service malwr.com. We uploaded a few samples to the website and also found some other reports from people who uploaded similar samples. As far as we know, most of the samples are following similar patterns of behaviour. In this blogpost we focuse on this sample - because we found it on an ICS and took a deeper look at it.
The file is 1578496 bytes (~1.6 MB) big and is identified as PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows.
1 2 3 4 5 | |
Sample’s hash sums
1 2 3 4 5 6 7 8 | |
As we might know, one should not run the command “strings” on an unknown file. That’s why we used the helpfull features of radare2.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 | |
As we can see, the .rsrc ressource section is with around 1,4 MB the biggest one. Let’s take a more closer look at it, but before that, we have to extract it. We can use wrestool :
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 | |
In this case we see many small files, but there is one which seems to be the most interesting one: The one with the suffix “RCDATA1”. wrestool identified most resources as icons, but only two look like valid folder-icons. These icons seem to be used to trick some users (social engineering) to think that the program is a folder - to initiate a double click.
In some modern webbrowsers, e.g Firefox, there is a built-in protection: It shows that the file is an application despite having a folder icon.
The extraordinary big file also seemed to be a windows-executable:
1 2 3 4 5 | |
If one searches for the MD5-hash 3afeb8e9af02a33ff71bf2f6751cae3a, one can find a program with the name NsCpuCNMiner32.exe. We will find out the purpose of this program later.
The strings from the .data section. There are some interesting entries!
For example which domains are used for communication:
1 2 3 4 5 6 7 8 9 | |
In the malwr.com log you can see, that there is a HTTP-request to the following URL: httpx://stafftest .ru/test.html. We can find the same entry in the binary:
1
| |
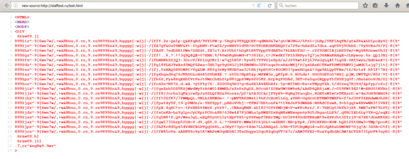
If you request this URL in a secure environment you get HTML sourcecode and a lot of gibberish. An analysis of Fortinet shows that only some characters need to be interchanged in order to get the cleartext - it seems to be a ROT47 chiffre with a modified charset and it can be reverted by runnning the following program:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | |
There’s an example run in our paste.
1
| |
Furthermore, a HTTP-request with multiple parameters is performed. The parameters seem to be the version ver, the computer’s name pc, the user name user and some more. We think that these values are used for the backend - so that the cybercrimials have an overview of how many and which kind of systems are infected. The parameter ver also indicates that the malware’s development is quite professional (with new releases and such). GuardiCore’s analysis also points out that with every new version a few new mechanisms for spreading the malware are implemented.
[…]strings also contains NsCpuCNMiner again (it exists for 32-bit and aswell for 64-bit computers) and is placed in the %%TEMP%% directory.
1 2 | |
Before the miner can run, it needs a list of mining pools to use. A handful of initial mining pool addresses were hardcoded and placed with a shell command in a file called pools.txt, but more were fetched with the shown HTTP request.
1
| |
In order to attribute the solved blocks to the right account on the mining pool, an account-specific API-Key has to be used:
1
| |
Reddit users were able to find out a few other adresses and API-Keys which seem to belong to the same person or group.
The malware is bruteforcing poorly configured FTP servers with the following usernames:
1 2 3 4 5 6 7 8 9 | |
and passwords:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 | |
The following strings of typical filetypes on a webserver might be a sign that the malware is changing their content to hide or spread itself.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | |
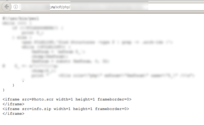
The manipulation consists of placing a 1x1 pixel sized Iframe, in which the malicious photo.scr is embedded. The code for that is:
1
| |
To achieve persistence, an autostart entry is created by using a registry entry. Additionally it tries to copy itself to all attached storage devices as seen below.
1 2 | |
Spreading methods and possible damage
The malware is using diffrent methods to infect other machines:
- Bruteforcing of FTP-servers (with wordlist)
- Copying itself to all attatched storage devices
- Using a 1x1 pixel sized Iframe within HTML-files to start an autodownload
- Setting up a wifi-hotspot (found in samples of GuardiCore)
In diffrence to ransomware, there is no visible damage, because the software only useses the CPU and only a tiny bit of storage - in general all services should work like before - only a bit slower. We also discovered the malware on Industrial Control Systemes - Viruses and trojans in such environments can become very dangerous if they try to spread aggressively.
It is not clear who the actual author is - but we think that the cybercriminals are really making a good profit off this mining botnet. It might be in a 6 or even 7-digits area.
We made a rough estimation and would like to share our calculation: We looked at the default mining configurations for monero and assumed that a great share of all infected systems might have a hashrate of 62 H/s (average dual core PC). (This hypothesis is very cautious, because gaming computers or server systems might have an even higher rate.) Furthermore we assumed a mining fee of 2%, which is also higher than normal, so a negativ aspect for the cybercriminals. If we use those preconditions and look at a mining calculator we get some interesting results:
1
| |
Assuming 50000 infected machines, one would generate up to 22000 $ a week.
1
| |
Because the threat actor has been active since last year or at least the beginning of 2016 (other reports of security experts point that out, for example GuardiCore), we can multiply it by the number of weeks passed in 2016 and we should have a quite good guess on how much the criminals may have earned. Of course one can also say that not all PCs are mining all the time and that AV engines might detect the virus - but the used assumption of 50000 infected machines could also vary and be much higher or lower in reality, partly because of the aggressive spreading techniques.
Some time ago Fireeye detected a malware sample from the same family - it used .top-domains for spreading. The command and control servers are the same as in our samples - so it is possible that it is the same threat actor or that it is kind of Malware as a Service Program (cybercriminal pay other cyberciminals for spreading their malware to victims)
Prevention and defense
The following list is a short overview of possible defense methods, in order to not get infected and to protect ourselfs from becoming part of an unwilling mining operation.
As a provider or administrator:
- Use strong passwords for FTP accounts
- Ban IPs which generate a lot of failed login attempts
- Blacklist the mentioned domains in your proxy service or firewall
- Keep the AV engine up to date
As an enduser:
- Be sceptical: Don’t open strange files with a double click
- Enable the option to show all file extentions in Windows
- Carefully use untrusted WiFis
- Don’t run autodownloaded scripts or applications
- Keep the AV engine up to date
The team of Internetwache.org