Today a lot of people buy things online in the internet. There are a lot of online shops and also some websites from parcel services, to track the shipment. Online orders are made by experienced just as well by inexperienced users so that they sometimes need to visit an unknown website. A situation like this would be perfect for cybercrimes to grab userdata. As we try to prevent bad boys from taking over important websites, we had a quick look at the website of DHL. That surely is in the interest of everybody, the users and the vendor.
The biggest parcel service in Germany is DHL (DHL International GmbH). The company is active in logistics and is part of the german Post AG. It’s maintaining a broad website with many practical functions for the users. There is the already mentioned tracking service, a newsletter system and also an onlineshop, where vulnerabilities are much more critical, because an attacker could gain access to user-data.
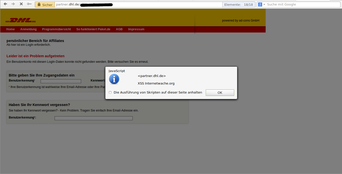
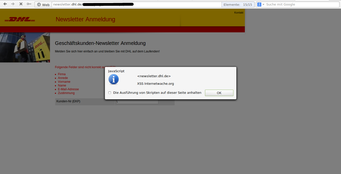
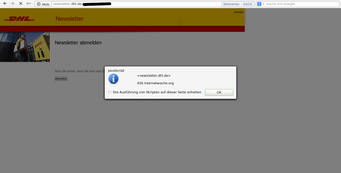
We began with the normal research for security issues and started to test the website and looked after conspicuous parameters. After a short time we noticed that the parameters often were filtered quite well, so that the injection of arbitrary code will not be that easy. However there were some exceptions so that we’ve ended up with 3 XSSes in total. The subdomains “newsletter.dhl.de” and “partner.dhl.de” were affected. Clever criminals (or better: annoying spammers) could have used these vulnerabilites to send spam mail and try to pish user-data.
We’ve reported the vulnerabilities directly to the responsible IT-security department of the “Deutsche Post” on the 23th of september 2012. One week later we noticed that the vulnerability has been fixed, but we were quite disappointed that nobody has responded to our email. We’re happy the vulnerabilites are now closed, but it gives us an ultra boost if the company replies and thanks us for the hints. We were even more happy that we finally received a friendly reply on the 11th of october 2012. They were sorry that the haven’t replied earlier and told us that they’re running own penetration tests, but somehow the parts of the website have not been tested.
So now we can put this case away and thank all involved persons for the good and competent coorperation.
Screenshots