Security is very important at Facebook. As the biggest social network in the world with 1.23 billion members, Facebook has been running a bug bounty program since 2011. Facebook announced they would pay a minimum of $500, with no upper limit. More than $2M has been paid out in rewards, including $1.5M in 2013 alone. As a security researcher you are very proud if you are able to help such a big company, it is also a nice reference and of course the rewards are also quite nice. So at one day we decided that we also want to paticipate in this bug bounty program and looked for vulnerabilities.
We took a deep look at the platform, but were not able to find anything, that might be because Facebook is a very popular target for many whitehat security researchers. But we do not gave up! So we find some nice minor issues on domains which are also owned by facebook.
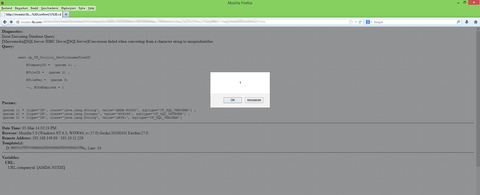
The first issue was located in a third-party subdomain on the fb.com Domain. (Nice to know: FB.com acquired by Facebook for $8.5M in 2010.) The subdomain: investor.fb.com and the issue was a limited redirection. The domain was structured like this:
1
| |
It was possible to change the parameters in the URL for example to this:
1
| |
With this small trick it was possible to redirect to every file which is stored in the third party system of: http://www.shareholder.com/. That way it might even be possible to store some fake data there and redirect to it. This system is also used by many other companies, so this bug does not affect only facebook. It was rewarded by facebook with 500$ as a low risk issue, but with a bit of social engineering or phishing it may have had a bigger impact.
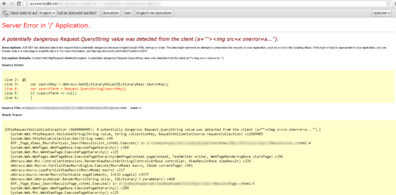
The funny thing is that @smiegles (a whitehat and good friend of us) found another bug in this system. His attention was drawn by @garagosy who thought about a vulnarablitity in the system aswell. It was a cool XSS ((Cross-Site-Scripting) which was rewarded with $500 (via filename and user agent, look at the screen).
It seems like we’ve missed some things there. However, “sharing is caring” and it’s nice to know that everybody has his own ideas to find vulnarablitities and that the crowdsourcing of bugs is quite efficient.
Then a few weeks ago we read in the press that facebook launched a new website to inform people about a smarter / connected world. It is called aconnectedlife.de and we’ve discovered two vulnarablitities there more or less by accident. One FPD (Full-Path-Disclosure) in the search and an XSS (Cross-Site-Scripting) in a swf file. Both bugs were rewarded with $500 and an entry in the Hall of Fame of facebook.com (https://www.facebook.com/whitehat/thanks/)
All in all one could say that the bug bounty program of facebook is quite fair to researchers and also very fast. We are proud that we could help facebook regarding their websecurity and hope that we also will find there some bugs in the future.
Happy hunting! The team of internetwache.org