The advertising service called Doubleclick was acquired by Google in 2007. That means that the corresponding domain is part of the googles bug bounty program.
After some research we discovered a nearly unexploitable XSS vulnerability, which we want to share with you. Maybe you’ll find a way to bypass the length limit of 7 characters.
If you want to try out how this “exploit” works follow the beneath instructions:
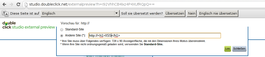
Open an external-preview page which is located under the subdomain “studio.doubleclick.net”.
E.g.
1
| |
Have you done this, click on “[change]” and choose “other site”. Enter you XSS exploit in the input field and hit “Go”. Try ”<h1>XSS</h1>” for better understanding of the length limit.
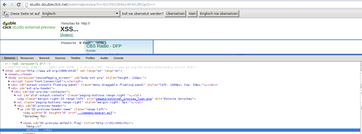
You should have noticed that the entered data is truncated after 7 characters and displayed back to the user.
If you didn’t use the mentioned h1-input, try it now.
If you take a look at the sourcecode you’ll see something like this:
You see that you have only 7 characters for creating a valid XSS exploit. The browser renderer’s tag-autocompletion helps us to close the missing tag, but it’s not bringing us any further.
As we were not able to build such a XSS exploit, we asked our lads, who did not seem to have an answer, too.
@soaj1664ashar @insertScript I'm looking for a xss vector which is only 7 chars long. Any ideas? #xss
— Internetwache (@internetwache) June 13, 2013
After all, we contacted Googles security team and they responded very fast saying that they consider this vulnerability very low risk.
Here’s a quote from their response:
1 2 3 4 5 | |
If you find a way to exploit this tricky XSS, you should submit it to google. In that case, we would appreciate it, if you share you working exploit with us.
Happy hacking,
The team of internetwache.org