During our tests of news we found the website of the public TV tranmitter N24. The website is an addition to the common TV show the broadcast system is hosting, and so the website offers many additional informations.
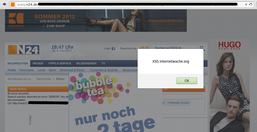
The page is ranked at position 350 in germany and at 7500 worldwide regarding to alexa.com. That implies that a lot of people are visiting n24.com to read the latest news. In the end we had a login bypass, a full path disclosure and a handful cross site scripting vulnerabilities on their website at the 8th of june 2012. The full path disclosure reveals some information about the system and the cross site scripting vector in the weather forcast would enable the attacker to steal the visitors cookies. The login bypass explains itself.
After we had sent the email to the “website support”, we did not receive any response within the following five days. After this first round, there was a new call to the IT-Company to reach the certain IT-Worker who is responsible for n24.com. He was quite surprised about our help , and we were aked for what company we would work. When we finished our call, he thanked us for our information, and at the same day we got an e-mail with good news. The problems would be removed and so at the 18.06.2013 we got a message with the information that everything was fine now.
We thank the comany for their trust in us and their nice cooperaiton and wish them all the best for the future.
The team of Internetwache.org
Screenshots