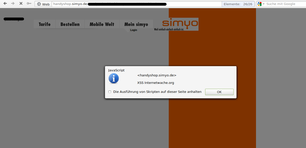
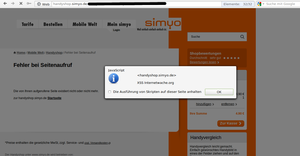
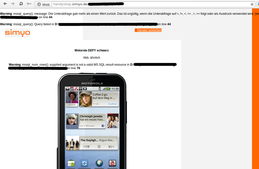
During our tests on telecommunication service provider, we discovered some flaws in Simyo’s onlineshop. Two reflected cross site scripting and one full path disclosure issues were found in their onlineshop, which runs under the subdomain “handyshop”.
In the first instance we contacted the company using their online contact form on 12th of August 2012. Somehow this approach has failed, because we did not receive any answer nor a fix within 3 weeks. We decided to use the power of social networks and contacted Simyo via twitter again. Some tweets later we had an email address to which we sent detailed information about the vulnerabilites (06th of september 2012). The day after we have received an email, that they’ve contacted the onlineshop’s vendor, who has fixed the vulnerabilites on the same evening. They told us, that the userdata was not at risk at any time and were very pleased about the responsible disclosure and as a thanks they sent a nice thank-you-gift.
We would like to thank Simyo for the gift and the fast fixes after our notifcation. Unfortunately they did not react to the contacting via their online contact form. Apart from that we can only give an account of their friendly and polite customer service and the very competent handling of security reports.
The team of internetwache.org
Screenshots