More than a year ago, we discovered a small XSS in Skype’s videomail API which landed us a warm place in Microsoft’s HoF.
Back then, Tim and Sebastian met up in Detmold to hack around a bit. Tim wanted to check out the new Skype feature Videomail and sent one to Sebastian. The email notification contained a link to a website and a PIN code.
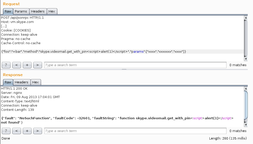
The website used the PIN code within an AJAX request to the host vm.skype.com. The request and the response was formatted in JSON and the responses had the correct application/javascript content-type set.
However, if you set the method parameter to an invalid value, the server would return a text/html response in JSON format telling you that the method couldn’t be found.
The request looked like that:
1 2 3 4 5 6 | |
To build the PoC we had to use a little trick to create a POST request with JSON parameters out of a normal html form.
1 2 3 | |
We simply add a new key/value pair by setting the input element’s name to {"foo":" and the value attribute contains the rest of the JSON string. Don’t forget to set the form’s enctype-attribute to text/plain. The final result is:
1
| |
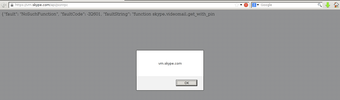
Screenshots:
Timeline:
- 09.08.2013 - Initial report
- 09.08.2013 - Case-ID assigned
- 19.08.2013 - Unconfirmed fix by the vendor
- 25.09.2013 - Vendor asks for fix confirmation - fixed
Over and out - Team of internetwache.org